|
A couple of days ago, Emil ‘Neex’ Lerner, a Russia-based security researcher, disclosed a remote-code execution vulnerability in PHP 7 – the latest iteration of the hugely popular web development language.
With this vulnerability, which has the CVE-ID of 2019-11043, an attacker could force a remote web server to execute their own arbitrary code simply by accessing a crafted URL. The attacker only needs to add “?a=” to the website address, followed by their payload.
Web servers using nginx and PHP-FPM are vulnerable and its documented in CVE-2019-11043. This exploit allows for remote code execution on some NGINX and php-fpm configurations. If you do not run NGINX, this exploit does not affect you.
Upgrade your php packages to the latest version. A new release that fixes the issue is released on 24th October. See https://www.php.net/archive/2019.php#2019-10-24-1
Upstream php packages with the fix are:
* 7.1.33
* 7.2.24
* 7.3.11
Site owners who are unable to update their PHP install can mitigate the problem by changing the nginx configuration.
This vulnerable NGINX and PHP-FPM configuration looks like the following example:
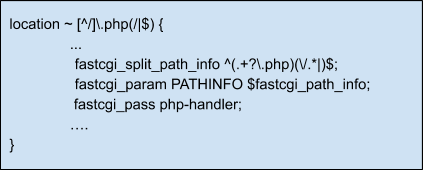
We should add $try_files $fastcgi_script_name =404; to mitigate this should become:
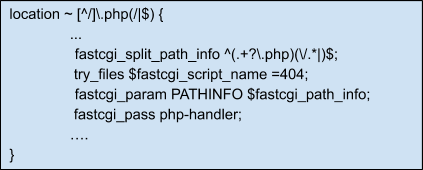
Then restart your web server and the issue will be mitigated.
|



